Investigation into Equifax Inc. and Equifax Canada Co.’s compliance with PIPEDA in light of the 2017 breach of personal information
PIPEDA Findings #2019-001
April 9, 2019
Overview
- On September 7, 2017 Equifax Inc. publically announced that an attacker had accessed the personal information of more than 143 million individuals,Footnote 1 including personal information for certain UK and Canadian residents. The number of affected CanadiansFootnote 2 was later estimated by Equifax Inc. to be 19,000, almost all of whom had their social insurance number, along with other accompanying identifiers, compromised.
- The Office of the Privacy Commissioner of Canada’s (“our Office” or “OPC”) investigation into this matter determined that the affected personal information of Canadians was collected by Equifax Inc. from certain Canadian consumers who purchased or receivedFootnote 3 direct-to-consumer products or fraud alerts from Equifax Canada Co. (“Equifax Canada”). We also found that Equifax Canada’s security infrastructure was highly integrated with that of Equifax Inc. In this context, at issue is the adequacy of safeguards by Equifax Inc. and Equifax Canada, as well as whether Equifax Canada had adequate accountability for Canadian data processed by Equifax Inc., and obtained valid consent for this processing from individuals. Given the age of certain information compromised in the breach, we also examined Equifax Inc.’s data destruction practices.
- Our investigation concluded that both Equifax Inc. and Equifax Canada contravened the Act with respect to all of the issues identified above. This report contains a number of recommendations to Equifax Inc. and Equifax Canada to address the contraventions found.
Background and Scope
- Nineteen individuals made complaints to our Office against Equifax about this matter, including five whose personal information was compromised during the breach. The complainants alleged that Equifax should not have allowed their personal information to have been compromised, that post-breach measures offered did not work properly for them as Canadians, and that they were surprised their information was in the US to begin with.
- The affected personal information was collected by Equifax Inc. from certain Canadian consumers who had direct-to-consumer products or fraud alerts. The direct-to-consumer products included paid online access by individuals to their Canada credit reportFootnote 4, credit monitoring, and alertFootnote 5 services (in relation to their Canada credit files). The information was collected by Equifax Inc. as it plays an integral role in delivering these direct-to-consumer products and processing certain fraud alert transactions.
- Attackers gained access to Equifax Inc.’s systems on May 13, 2017 by exploiting a known vulnerability in the software platform supporting an online dispute resolution portal that is part of Equifax Inc.’s Automated Consumer Information System (“ACIS”). They then operated undetected within Equifax Inc.’s systems for a period of time and ultimately gained access to Canadian personal information unrelated to the functions of the compromised portal.
- Information in Canadians’ credit files is stored by Equifax Canada on servers located in Canada and segregated from Equifax Inc.’s systems. However, during the process of delivering direct-to-consumer products to Canadians, information from credit files needed to fulfil these products is transferred to Equifax Inc. in the US. For instance, a static copy of a full credit file is transferred by Equifax Canada to Equifax Inc. if a credit report is purchased by a consumer. While Equifax Canada’s servers are segregated from Equifax Inc.’s systems, Equifax Canada’s security policies, direction and oversight were, and are, largely managed by Equifax Inc.
- With the above as context, this report examines the following issues.
Issues Examined in Relation to Equifax Inc.:
- Issue 1. Given the failure of security safeguards in this breach, whether the personal information of Canadians held by Equifax Inc. was protected by security safeguards appropriate to the sensitivity of the information as required by PIPEDA Safeguards Principle 4.7.
- Issue 2. Given the age of certain of the affected information, whether the personal information of Canadians was handled in conformity with the retention and destruction requirements of PIPEDA Principle 4.5.
Issues Examined in Relation to Equifax Canada:
- Issue 3. Given that the compromised Canadian information was collected by Equifax Inc. for the purpose of delivering Canadian products and fraud alerts, whether Equifax Canada demonstrated adequate accountability for protecting personal information of Canadians collected by Equifax Inc. and disclosed by Equifax Canada to Equifax Inc., as required under Principle 4.1.
- Issue 4. Whether there was adequate consent by Canadians for the collection of their personal information by Equifax Inc., and for the disclosure of their personal information to Equifax Inc. by Equifax Canada, as required under Principle 4.3.
- Issue 5. Given that the personal information of Canadians handled directly by Equifax Canada was managed by the same security policies, direction and oversight as for Equifax Inc., and given the failure of these safeguards in the breach, whether the personal information of Canadians held by Equifax Canada was protected by adequate security safeguards as required by Safeguards Principle 4.7.
- Issue 6. Given that the information compromised presents an ongoing risk of harm to affected individuals, whether the mitigation measures offered to affected individuals by Equifax Canada were adequate to protect their personal information from unauthorized use, such as for future identity theft, as required by the Safeguards Principle 4.7.
Jurisdiction
- Equifax Inc. is incorporated in the US, and is the parent company of Equifax Canada, which is incorporated in Canada. We note that in relation to this matter, PIPEDA applies to both the personal information handling practices of Equifax Canada, and the personal information handling practices of Equifax Inc. With respect to Equifax Inc., we note in particular that Equifax Inc. collected personal information from Canadians for the purpose of facilitating the delivery of products in Canada.
Methodology
- In coming to its conclusions over the course of investigation, the OPC considered information from a variety of sources provided by both Equifax Inc. and Equifax Canada, including:
- Written representations to our Office, including in response to an OPC Order for Production;
- Interviews with key staff, both by phone and/or in person during on-site visits to Equifax Inc. and Equifax Canada headquarters;
- Post-breach assessments from three third parties hired by Equifax Inc.;
- The compromised data itself;
- Copies of internal and external policies, training material, reports, risk assessments and certifications prepared by Equifax Inc., Equifax Canada, and by third parties on their behalf.
Section 1. Safeguards for Canadian Personal Information held by Equifax Inc.
- Under the PIPEDA Safeguards Principle (4.7) personal information must be protected by security safeguards appropriate to the sensitivity of the information.
- The Canadian information compromised in the breach included a billing table containing payment card information of Canadians who paid a fee by phone to either place a fraud alert on their Canadian credit file, or to purchase Canadian direct-to-consumer products. Direct-to-consumer products are only available through Equifax Inc.’s Global Consumer Solutions system (“GCS”), the trade name for Equifax Consumer Solutions, LLC (“ECS”), a US-based subsidiary of Equifax Inc.
- Our investigation determined that Equifax Inc. held the following types of personal information of Canadians:
- payment card information used to purchase Canadian products and fraud alerts, and related transactional information;
- account information of Canadians who created accounts to access Canadian products online, including user names, passwords, and information the individuals provided for identity matching, including social insurance numbers in most cases; and
- copies of full credit reports and credit alerts viewed by Canadians through their online accounts.
- These combinations of information are sensitive. If placed in the wrong hands they pose a real risk of harm through identity theft. In addition, the information is reputationally sensitive, as it includes, in many cases, detailed information about individuals’ credit worthiness. In this context, under PIPEDA, the security safeguards in place by Equifax Inc. to protect this personal information should be commensurately high.
- The breach began with attackers exploiting a publically known vulnerability in the Apache Strut software platform supporting Equifax Inc.’s online dispute resolution portal, a component of its Automated Consumer Information System. This portal is the method for US consumers to dispute the accuracy of information in their US credit file – it is not used by Canadian consumers. Equifax Inc. was notified of the vulnerability and the related patch to correct it on March 8, 2017.
- The attackers gained access on May 13th 2017, more than two months after the above notification, and were subsequently able to operate undetected within Equifax Inc.’s systems for approximately 77 days. During this time, they were able to access personal information held in several hundred database tables, across a significant number of Equifax Inc. databases.
- The attackers were also able to access approximately 11,000 files saved by Equifax Inc. IT staff to a ‘file share’ between April 29, 2010 and September 16, 2016. A ‘file share’ is a network storage area where multiple users can save, modify or delete files. The files were saved for a range of purposes, and not subsequently deleted. Of these files, 28 were identified by Equifax Inc.’s forensic analysis as including up to 100,000 points of data that were potentially personal information of Canadians (including possible ‘dummy data’ and duplicate information). It later indicated that that total included confirmed personal information of approximately 8,000 Canadians.
- The attack was detected by Equifax Inc. on July 29, 2017 when an expired Secure Sockets Layer (“SSL”) security certificate was belatedly updated. Updating the certificate rendered previously undetected suspicious traffic noticeable. Equifax Inc. fully contained the attack the following day.
- The path of the attack described above highlights a range of unacceptable deficiencies in Equifax Inc.’s security program. Specifically these include:
- Inadequate vulnerability management - to prevent attacks through known vulnerabilities.
- Inadequate network segregation - to reduce the scope of access and harm in the case of a breach.
- Inadequate implementation of basic information security practices – to be able to appropriately manage the use of personal information and identify potential unauthorized use.
- The broad range of these deficiencies also highlights the fundamental failure of the oversight mechanisms that should have been in place to:
- accurately assess the security risks faced;
- ensure that the security program was adequate to protect the sensitive personal information held by Equifax Inc. against these risks; and
- ensure that the security program, including relevant security policies, was implemented in practice.
Vulnerability Management
- Known vulnerabilities present a significant risk for organizations due to the proliferation of information on how to exploit such vulnerabilities. All organizations holding personal information must have robust systems in place, either internally or through external service providers with appropriate expertise, to address known vulnerabilities on a continuous basis. Such systems must ensure that known vulnerabilities in all internet-facing service platforms, operating systems, and applications presenting any risk of exploitation are corrected in an expedited manner. This must include mechanisms to:
- accurately and expeditiously identify vulnerabilities in need of correction;
- implement appropriate fixes to correct identified vulnerabilities in an expedited manner; and
- verify that vulnerabilities have been fixed.
- In the case of the vulnerability exploited by the attackers, Equifax Inc. confirmed that it was aware of the vulnerability in question and sent an internal alert for the patch to be applied. However, Equifax Inc. did not have mechanisms in place to automatically patch such vulnerabilities, and for the affected online dispute resolution portal, employees failed to manually patch the vulnerability. Further, at the time, Equifax was using only a single vulnerability assessment tool, which was limited in scope. This tool failed to detect that the vulnerability remained, as it did not check the correct virtual subdirectory.
Network Segregation
- Network segregation uses virtual or physical barriers to limit the flow of information between different parts of a computer network, the way bulkheads in a ship limit flooding if the hull is breached. To protect personal information, organizations should institute network segregation that meaningfully segregates databases containing personal information based on sensitivity and function.
- In the case of this breach, the attackers were able to access information in hundreds of database tables held outside the breached application server. At the time, while there were firewalls separating databases from each other and from the breached portal, they did not meaningfully segregate the network as they were configured to allow a broad range of queries (including requests for data from the attackers) to flow between the databases and the breached server. This effectively made these firewalls “glass walls” - while the attackers couldn’t go through them, they could still see and take copies of what was behind them.
- Equifax Inc. contended that the open firewall configurations allowed them to use information in other databases to detect and prevent fraud in the compromised online dispute resolution portal. We accept that information in a few of the affected databases could have been useful for this purpose. However, Equifax Inc. indicated that it did not have a network map showing its relevant network architecture including firewalls at a level of specificity necessary for our Office to fully analyse the scope of incident, and could not easily identify which databases had been accessible in the incident.
- Moreover, the online dispute resolution portal cannot be used by Canadian consumers, and Canadian personal information would therefore not have been relevant to fraud detection on it. The Canadian data should therefore have been fully segregated from the affected application server.
- In general, consideration should also be given to segregating all of one organization’s consumers’ information from that of other organizations – to limit exposure to potential threats through unrelated applications or processes. This is particularly appropriate where large volumes of information are involved, and processing varies between organizations, as is the case here.
- In addition, considering the volume and sensitivity of personal information held by Equifax Inc., safer methods should have been used to facilitate fraud detection while maintaining meaningful network segregation - such as using an intermediary application that would only return the limited information specifically needed for fraud detection.
Implementation of Basic Information Security Practices
- PIPEDA Principle 4.7 requires that methods of protection should include physical measures, such as restricting access using locks, organizational measures, such as limiting access on a “need-to-know basis, and technological measures, such as the use of passwords and encryption”.
- In addition to the specific issues described in the previous paragraphs, while examining systems and safeguards relating to the breach and the handling of Canadian personal information, our investigation found indicators of poor implementation of these basic methods of protection. We found multiple instances of practices by Equifax Inc. that did not meet basic standards for such methods of protection as laid out in internationally accepted security standards. Examples of these issues are provided below (para. 37 - 42).
- For instance, as part of responsible access controls, it is a basic information security practice to know who is saving and modifying files when they involve personal information. For many of the 28 files containing apparent Canadian information in the compromised ‘file share’, Equifax Inc. could not conclusively identify who had saved the files or why.
- It is also basic access control practice that staff and customers’ usernames and passwords be stored securely. Equifax Inc.’s forensic investigation found unencrypted usernames and passwords saved in the ‘file share’ - accessible to multiple people (and, in this case, the attackers).
- In addition, it is a basic information security practice to keep production data (i.e. real personal or business information) separate from test data (fictitious information used for developing and testing applications and IT systems). The compromised ‘file share’ contained both in the same environment.
- It is also fundamental information security management to provide effective training for staff. Equifax Inc. claimed that it did provide staff with training on appropriate handling of data, but was unable to provide any evidence of structured training for its IT staff on appropriate practice for use of file shares, such as training materials or curricula.
- Keeping SSL certificates up-to-date is also a basic information security practice. A contributing factor to the length of time that the attackers were able to operate undetected was that an internal SSL certificate had not been renewed, despite the fact that Equifax Inc. represented that its policy is to routinely update SSL certificates.
- And finally, the Canadian credit card information of individuals who purchased certain direct-to-consumer products or fraud alerts by phone was, at the time, held by Equifax Inc. in a database that had not been included in the scope of Equifax Inc.’s annual Payment Card Industry Data Security Standard (PCI-DSS) certification. Industry standards require that this certification cover all systems used by an organization to handle credit card information. The forensic third party hired by Equifax Inc. which conducted an analysis after the breach, found deficiencies in compliance with the PCI-DSS standard.
Oversight Mechanisms
- Our investigation found that Equifax Inc. had security policies in place that set, at a high level, general expectations for the management of information security. Equifax Inc. represented that between 2014 and 2017 it had tripled its combined operational and capital expenditures on IT security and nearly doubled its security staffing. Despite this, our investigation found the multiple security deficiencies identified above (para. 27 - 42) across a wide range of domains. In our view, the existence of a clear disconnect between policies and practices in a range of security domains demonstrates that Equifax Inc.’s security program had critical gaps, and that therefore the oversight mechanisms were inadequate.
Conclusion
- For the reasons described above, we are of the view that Equifax Inc.’s safeguards were lacking in the following four areas:
- vulnerability management;
- network segregation;
- implementation of basic information security practices; and
- oversight.
- In our view, the specific weaknesses described above individually and collectively constitute failures to implement appropriate security safeguards given the volume and sensitivity of the personal information held by Equifax Inc. Consequently, in relation to the safeguards of personal information by Equifax Inc., the matter is well-founded.
- Since the breach, Equifax Inc. has taken a range of steps to improve its security program, including:
- moving to a 24/7 information security model;
- enhancing vulnerability management processes and procedures;
- enhancing network segregation, as well as increasing restrictions and controls for accessing data housed within critical databases, and reducing the scope of data retained in the backend databases;
- instituting a tiered structure of oversight mechanisms with enhanced risk assessment and internal audit functions; and
- applying a range of other technical improvements to its logging, detection, and access control tools and practices.
- While the above are positive steps, in light of the serious deficiencies found, which are indicative of long-term systemic issues, we are of the view that additional assurances are required to ensure Equifax Inc.’s safeguards are brought up to an adequate level. Our recommendations on appropriate measures to achieve this are identified in Section 3 of this report.
Section 2. Retention of Personal Information by Equifax Inc.
- PIPEDA Principle 5 – Limiting Use, Disclosure, and Retention, requires, in Principle 4.5.3, that personal information that is no longer required to fulfil the identified purposes should be destroyed, erased, or made anonymous, and that organizations shall develop guidelines and implement procedures to govern the destruction of personal information.
- As described above (para. 23), one source of the compromised Canadian personal information – accounting for approximately 8000 of the affected Canadians – was data found in 28 files saved to a file share between April 29, 2010 and September 16, 2016. Given the age of certain files, which Equifax Inc. identified as being broadly related to system maintenance, troubleshooting and application updates, we examined Equifax Inc.’s retention practices for Canadian personal information more broadly.
- Equifax Inc. has a Global Retention Policy (“retention policy”) which sets out how long certain records should be retained. At the relevant time, with respect to Canadian data held in the GCS, it specified that account registration information should be destroyed after five years, other account information after two years, and credit reports or alerts contained in GCS accounts after one year. The policy also identified that the ‘record owner’ was responsible for implementation of the retention policy for any particular record, and identified that compliance with the policy should be monitored.
- Our Office interviewed an Equifax Inc. IT Architect Specialist for GCS. This individual was identified by Equifax Inc. as someone who could respond to our questions concerning the management of personal information under the GCS system. In response to our questions, he confirmed that, to his knowledge, in the GCS databases, there was no process in place to delete Canadian personal information in compliance with Equifax Inc.’s retention policy. Further, he confirmed that despite retention periods set in the policy having expired for many records, no Canadian personal information held in the GCS databases had been deleted since at least 2010 when the GCS system was moved to its current platform. He noted that he was aware of plans being developed to institute some destruction practices – in order to be compliant with the European General Data Protection Regulation 2016/679, but that these efforts were limited to European personal information.
- Neither the IT Architect Specialist, nor Equifax Inc.’s Chief Information Officer for the GCS were able to identify who the ‘record owner’ was, as per the retention policy, for personal information held in the GCS databases. Further, the employee responsible for GCS regulatory compliance in the US and Canada stated that she was not sure who at Equifax Inc. was responsible for the compliance functions described in the retention policy.
- It was evident during our investigation that key staff lacked adequate knowledge and awareness about the retention policy, that the policy was not being respected and that monitoring for compliance was not being carried out.
- In light of the failure of Equifax Inc. to implement its retention policies, with respect to compliance with the retention and destruction requirements of PIPEDA Principle 5, the matter is well-founded.
- Our recommendations on appropriate measures to address this contravention are identified in Section 3 of this report.
Section 3. Accountability of Equifax Canada for Canadian Personal Information Handling by Equifax Inc.
- PIPEDA Principle 1 – Accountability, states, that an organization is responsible for personal information under its control and shall designate an individual or individuals who are accountable for the organization’s compliance with the following principles. Further, Section 4.1.3, states that an organization is responsible for personal information in its possession or custody, including information that has been transferred to a third party for processing. The organization shall use contractual or other means to provide a comparable level of protection while the information is being processed by a third party.
- Given that the Canadians affected by the breach at Equifax Inc. were individuals who had obtained Canadian direct-to-consumer products or fraud alerts we examined compliance with these accountability requirements. As noted above, in this report, “Canadians” refers to individuals with a Canadian credit file held in Canada by Equifax Canada (not, for instance, Canadian citizens residing in the US with a US credit file).
- First, we considered whether Equifax Inc. is a third party with respect to Equifax Canada. We are of the view that for the purposes of personal information handling under PIPEDA it is a third party, for the following reasons:
- Equifax Canada and Equifax Inc. are separately incorporated in different jurisdictions.
- Although both the Privacy Policy and Terms of Use available to Canadians on Equifax.ca at the time of the breach make reference to the possibility of Equifax Canada partnering with affiliates in the delivery of products, both represent that such affiliates, including Equifax Inc., are separate entities (see further details in para. 104-105).
- For the purposes of personal information handling, Equifax Canada has consistently represented, both to our office, and to the public, that the Equifax Canada Chief Privacy Officer is the designated individual accountable for the handling of personal information by Equifax Canada.
- Second, we considered whether Equifax Canada had control and was responsible under Section 4.1 of PIPEDA, for the Canadian personal information collected by Equifax Inc., and transferred to Equifax Inc. by Equifax Canada, for the purposes of fulfilling the Canadian direct-to-consumer products.
- Equifax Canada and Equifax Inc. offer a range of products to both organizations and individuals, such as credit check services to lending organizations, and direct-to-consumer products to individuals. Direct-to-consumer products for Canadians include online access to a consumer’s Equifax Canada credit report, as well as credit monitoring of a consumer’s Equifax Canada credit file. Credit monitoring is a package of services. The main component of credit monitoring is proactive alerts to the consumer about certain activity on their Equifax Canada credit file, such as a new credit check, that could alert the individual to someone else trying to get credit in their name.
- Products provided to organizations (lenders), are delivered by Equifax Canada directly, with any related personal information stored on computer systems located in Canada. Canadian direct-to-consumer products however, are delivered through an online portal operated by Equifax Inc. At the time of the breach, Equifax Inc. also handled fee payments made by phone for Canadians to place a fraud alert on their Equifax Canada credit file – collecting and processing the related payment and transactional information.
- Canadians interested in obtaining Canadian direct-to-consumer products are directed to a portal hosted by Equifax Inc.’s Global Consumer Solutions (“GCS”) system to begin the application process. Consumers applying by phone are guided through the same process by customer service agents.
- The portal, which is hosted in the US by Equifax Inc., collects and stores all information an individual submits through the process of purchase, account set-up, and authentication. Equifax Canada then subsequently discloses personal information to Equifax Inc., including copies of the consumer’s credit report, or credit alertsFootnote 6 as needed to fulfil the consumer’s order (e.g. when a consumer goes to their portal to view their credit report, a fresh copy is sent to Equifax Inc. from Equifax Canada – see Figure 1). In practice, these products are then stored by Equifax Inc. indefinitely (as described in Section 2 of this report).
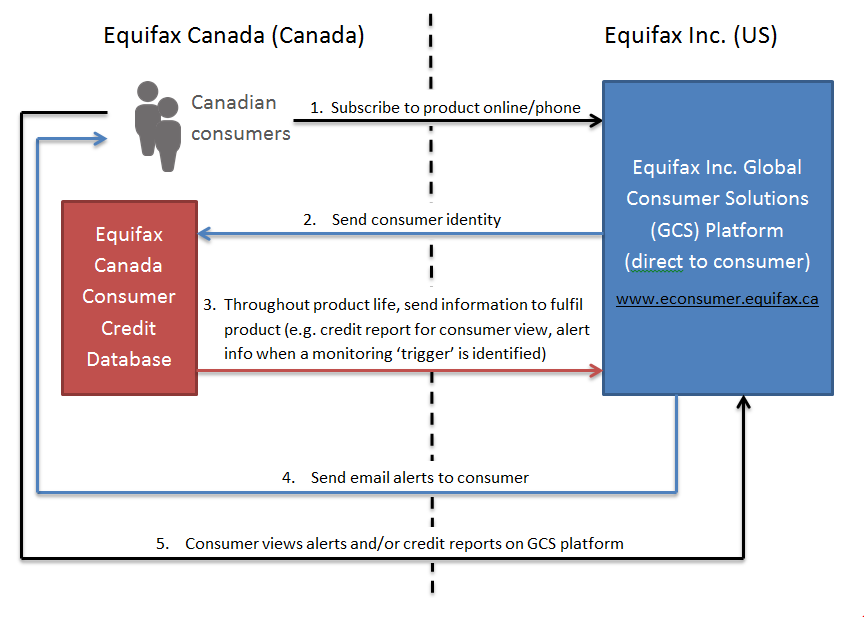
- Equifax Canada and Equifax Inc. contend that individuals obtaining Canadian direct-to-consumer products were contracting for these products directly with Equifax Consumer Solutions LLC (“ECS”), a US-based Equifax Inc. subsidiary. They contend that the Canadian information held by Equifax Inc. was therefore not under Equifax Canada’s control, as it simply communicated credit report information to ECS which was a reseller acting on its own behalf, not on behalf of Equifax Canada.
- However, Equifax Canada indicated that at the time of the breach it had no written agreement with Equifax Inc. describing this reseller relationship. More significantly, at the time of the breach, the entire process of signing up for a direct-to-consumer product took place on “Equifax.ca” webpages, and the Terms of Use Canadian consumers agreed to upon purchasing direct-to-consumer products specifically indicated that “The products and product features (“Product" or "Products") available via this Site are provided by Equifax Canada Co. (“Equifax”). We may also partner with other companies (“Suppliers”) or affiliates (“Equifax Affiliates”) to provide Products to you or sell you a Product provided by a Supplier or an Equifax Affiliate.”
- Equifax Canada contends that this statement of responsibility was accidental. It explained that previously, specifically between May 2013 and June 2016, Canadian consumers who obtained direct-to-consumer products would have been asked, at the end of the application process, to agree to a different “Product Terms of Use” (“Product Terms”). That Product Terms stated: “You accept and agree to these terms and conditions and Equifax Canada’s Privacy Policy, which together form a contract between you and Equifax Consumer Services LLC, a United States corporation (“Us” or “We”).” It indicated that in a June 2016 website update, the link to the Product Terms was accidentally replaced with a link to the Terms of Use described in para. 65, which, at the time, were much briefer and did not include product details.
- However, those brief Terms of Use were then thoroughly revised two months later, in August 2016, to include the detail formerly provided in the “Product Terms of Use” – while retaining the opening declaration described in para. 65 that the products were provided by Equifax Canada.Footnote 7
- Further, between at a minimum February 2011 and September 2015, the publically available Equifax Canada Privacy Policy clearly indicated that Equifax Canada was providing the direct to consumer products, stating that the Policy applied “to consumer credit information collected, used and disclosed by Equifax Canada” and that it “addresses how Equifax collects, uses and discloses personal information that you provide to us as a consumer when accessing our services and products directly.” Throughout this period the Privacy Policy included no reference to Equifax Inc., ECS, or to the potential for transfers of personal information to any organizations for the delivery of products. It further defines the Equifax Canada Chief Privacy Officer (“CPO”) as “…the person designated by Equifax and assigned responsibility for ensuring Equifax's compliance with PIPEDA requirements.”Footnote 8
- We note in addition, that ECS plays functionally the same role in the delivery of direct-to-consumer services to UK residents using data collected by Equifax Ltd (incorporated in the UK), and in this role, it is designated as a processor on behalf of Equifax Ltd.Footnote 9
- Given the above, in our view, for the purposes of PIPEDA section 4.1, Equifax Canada remained in control - responsible and accountable for the handling of personal information by Equifax Inc. in the course of offering Canadian direct-to-consumer products for the following reasons:
- The Canadian direct-to-consumer products in question are, effectively, ‘facilitated access’ for individuals to understand: (i) what personal information Equifax Canada is collecting about them, (ii) what inferences Equifax Canada draws about their credit worthiness, and (iii) who Equifax Canada discloses their information to in the form of credit checks. In our view, these products are therefore highly connected to Equifax Canada’s business. In this context, Equifax Canada remains in control of the personal information in question.
- In some documents, at some times (including the Product Terms referenced in para. 66), Equifax Canada has referenced the participation of other affiliates in offering direct-to-consumer products to Canadians. However, these references were contradicted by Equifax Canada’s continuous and prominent representations to consumers that it was providing the products to Canadians and its representations about the role of the Equifax Canada’s Chief Privacy Officer,
- In our view, either a. or b. above would, separately, lead to the clear conclusion that the handling of the personal information to deliver Canadian direct-to-consumer falls under the control and responsibility of Equifax Canada. Therefore, in this context, both the information transferred by Equifax Canada to Equifax Inc., and the information collected directly by Equifax Inc. to deliver these products, falls under the custody of Equifax Canada for the purposes of Section 4.1.3 of PIPEDA.
- In relation to this analysis, we note that the overarching Accountability Principle states, in Section 4.1, that an organization is responsible for personal information under its control and shall designate an individual or individuals who are accountable for the organization’s compliance with the PIPEDA principles. It is therefore a key aspect of accountability that the individual designated by the organization, in this case, Equifax Canada’s CPO, must have tools and structures in place to enable him or her to be truly accountable for the handling of personal information.
- In this context we examined the nature of the controls put in place by Equifax Canada, including the role of its CPO, to ensure that Canadian personal information processed by Equifax Inc. receives a level of protection comparable to that required under PIPEDA.
- To determine the appropriate level of controls, consideration must be given to both the scope and sensitivity of personal information being handled. In some cases where the third party is closely affiliated and the personal information being handled is of limited scope and sensitivity, it may be possible to rely on light controls and pre-existing, adequate, policies and practices of the third party to fulfil the obligations under 4.1.3.Footnote 10 In a case where a substantial volume of sensitive personal information belonging to a large number of individuals is being handled over a prolonged period, the level of controls should be commensurately high. In such a situation, in our view, PIPEDA Principle 4.1.3 requires, at a minimum:
- A formal written arrangement, updated periodically and in the case of material changes, which should generally include details about the following:
- what personal information is being handled by the third party, including both information shared by the organization and any information collected directly by the third party on behalf of the organization;
- what specific rules, regulations and standards need to be complied with in the handling of the information, including PIPEDA;
- the roles and responsibilities of key stakeholders within both organizations for the handling of the personal information, including responsibilities for specific functions, decision-making, safeguards and breach response;
- information security obligations;
- acceptable uses of the information;
- retention and destruction obligations; and
- reporting and oversight arrangements to ensure compliance with the above, including reporting obligations in the case of a breach that could compromise the personal information.
- A structured program for monitoring compliance against the obligations laid out in the arrangement. The program should be suitable to the scope and sensitivity of the personal information being handled. It should include:
- mechanisms for periodic reporting by the third party on the handling of the personal information; and,
- where scope and sensitivity of the personal information handled is significant, mechanisms to ensure periodic external assessment (by the organization or an appropriate third party) of compliance with the full range of obligations described in the written arrangement.
- A formal written arrangement, updated periodically and in the case of material changes, which should generally include details about the following:
- Equifax Inc. estimated that at the time of the breach, it held the personal information of approx. 2.4 million Equifax Canada consumers. As noted in previous sections of this report, the information was sensitive. Equifax Canada should therefore have had a robust accountability framework as described above for the information transferred to, and collected on its behalf by, Equifax Inc.
- At the time of the breach, Equifax Canada’s Privacy Policy stated: “In the event that we transfer your personal information to a third party in Canada or across borders for processing, we contractually require such third party to protect your personal information in a manner consistent with our privacy safeguarding measures, subject to the law of the third party jurisdiction.” In our view, contrary to this statement, Equifax Canada did not have a formal written arrangement with Equifax Inc. with respect to the handling of Canadian information.
- Equifax Canada stated that Equifax Inc.’s policies and practices were sufficient to ensure compliance with Canadian law. In our view, this reliance on Equifax Inc.’s policies and practices meant there was no clear framework within which Canadian law was being applied, creating significant accountability gaps. Specifically, Equifax Canada had mechanisms in place to address some, but not all, of the elements above (para. 74).
- For instance, with respect to appropriate use of personal information, now, and at the time of the breach, Equifax Canada has processes whereby proposed new or modified uses of Canadian personal information by Equifax Inc. or Equifax Canada are reviewed by legal and privacy staff. New programs that would use Canadian personal information are assessed for compliance with PIPEDA principles – such as making social insurance numbers optional in forms specific to Canadians.
- With respect to identifying rules, regulations and standards that must be complied with, Equifax Canada indicated that its legal and privacy team had provided training for Equifax Inc. staff on Canadian legal and regulatory requirements including privacy. In addition, Equifax Inc. conducts an annual review of its data security policies, which the Equifax Canada CPO contributes to from the perspective of Canadian requirements. However, it was unable to describe any of these contributions, citing that all documentation of any such contributions had been purged due to its one-year retention policy for internal emails.
- However, during the course of the investigation, Equifax Canada was, in several instances, either unable or unwilling to provide clear and timely explanations to our office about basic accountability matters such as: (i) how the Canadian personal information came to be held by Equifax Inc., and (ii) how it came to be affected by the breach. Further, Equifax Canada failed to provide our office with timely access to key systems, documents and data controlled by Equifax Inc. relating to the security of Canadian information.
- In addition, our investigation found a range of other significant gaps in accountability for the handling of Canadian personal information:
- Breach Response: Timely and comprehensive breach response can reduce the risk to individuals affected by a breach, and relies on effective coordination and communication where there are multiple parties involved. In this instance, the Equifax Canada CPO was not notified by Equifax Inc. of the breach until hours before Equifax Inc. went public on September 7, 2017, despite the fact that Canadian personal information was known to be affected.
- In addition, even after Equifax Canada was notified of the breach, there were continued failures of communication with respect to breach response affecting Canadians. For instance, Equifax Inc. was aware, as of September 19, 2017, that Canadian personal information could be included in a compromised billing table of credit card transactions. Canadians were clearly identifiable in the table by their addresses.
- Despite the evident compromise of Canadians’ information, Equifax Inc. failed to involve Equifax Canada in subsequent breach notification to these individuals, and, on October 23, 2017, issued letters to them at Canadian addresses. These letters included inaccurate information, such as inviting them to access credit monitoring through a portal Canadians were unable to use because it was set-up for Equifax Inc. consumers only. Only after receiving complaints from these individuals did Equifax Canada realize what had happened, and re-notify the affected 11,000 Canadians. Other Canadians were told by Equifax Canada that their online account, hosted by Equifax Inc., had been locked for their protection when it had not been. Equifax Canada should have had effective mechanisms in place to validate that post-breach communications to Canadians were accurate, and that protective measures put in place for them were properly implemented.
- Clarity about scope of personal information handled: Understanding what is being processed, and why, is a fundamental building block of accountability. During the investigation, Equifax Canada provided conflicting information about the purposes for which Equifax Inc. held the Canadian personal information compromised in the breach.
- Specifically, more than 4 months after the detection of the breach, Equifax Canada represented to our office that all of the 19,000 affected Canadians had obtained direct-to-consumer products from Equifax Canada through Equifax Inc.’s Global Consumer Solutions (GCS) system. However, this statement is contradicted both by complainants’ representations, and other documentation provided by Equifax Canada,Footnote 11 which both demonstrated that certain affected individuals did not have direct-to-consumer products through GCS, but rather, had only paid a fee for Equifax Canada fraud alerts by phone. The personal information collected and retained by Equifax Inc. for the processing of fraud alert payments was significant, going beyond payment card information to including details such as individuals’ social insurance numbers. After we raised the inconsistency, Equifax Canada corrected its earlier statement, confirming that Equifax Inc. handled both the personal information of (i) Canadians with direct-to-consumer products, and (ii) Canadians who paid for fraud alerts by phone. This difficulty in providing clarity about the scope of Equifax Inc.’s involvement in processing Canadian personal information is of concern, as a clear understanding what is being processed, and by whom, is a necessary foundation to effective accountability.
- Clarity about roles and responsibilities: Clarity about who does what and who is responsible is also critical to ensuring effective accountability. We found a lack of clarity among Equifax Canada staff about roles and responsibilities with respect to the handling of Canadian personal information by Equifax Inc. For instance, the current Equifax Canada CPO indicated during the investigation that Equifax Canada was not responsible for the handling of any Canadian personal information collected directly by Equifax Inc., despite the clear indications, summarized in para. 70 above, that such accountability was required under PIPEDA. In our view, as Equifax Canada is the controller for this personal information, Equifax Canada’s designated Privacy Officer, the Equifax Canada CPO, is accountable for the personal information, wherever it is held or processed.
- Monitoring: When a third party is handling personal information for an organization, it is important that the organization have measures in place to periodically ensure that the third party is actually fulfilling its obligations to protect that personal information. This could include reviewing reporting from the third party on information handling, third party audits or certifications against clearly laid out obligations, or direct oversight of the third party on a periodic basis. Where, as in this case, the third party is continuously processing a significant volume of sensitive personal information, these measures must be commensurately robust. Such measures can be used by the designated Privacy Officer to ensure they fulfil their accountability role wherever information is held.
- Equifax Canada indicated that it does not conduct any monitoring for compliance by Equifax Inc. with Canadian personal information handling requirements under PIPEDA once information has been transferred to, or collected by, Equifax Inc. In this context, our investigation found, for instance, that Equifax Inc. had taken no meaningful steps to delete Canadian personal information in accordance with a retention schedule as required under PIPEDA (see Section 2 of this report).
- With respect to monitoring Equifax Inc.’s compliance with PIPEDA’s information security requirements, Equifax Canada’s actions were limited to the receipt of tri-annual certificates of compliance with the ISO 27001 information security standardFootnote 12 (provided by EY CertifyPoint, an Ernst & Young company). In our view, it would generally be reasonable, for the purpose of assessing a third party’s compliance with PIPEDA’s safeguards requirements, for an organization to rely on an up-to-date security certification conducted under the following conditions: (i) by an appropriate party, (ii) against an appropriate security standard, and (iii) in the absence of contradictory indicators of security concerns.
- The standard used in this case, ISO 27001, is appropriate, as it is specific to information security, comprehensive, peer reviewed, regularly updated, and broadly recognized. The organization which conducted the certification, EY CertifyPoint, is a firm with substantial relevant expertise, and the audits were conducted annually.
- However, in this case, Equifax Canada was also privy to other information about Equifax Inc.’s security practices which clearly cast doubt as to whether Equifax Inc. remained ISO 27001 compliant. Specifically, it had access to external penetration tests and internal audits (conducted by other firms with relevant expertise), covering Equifax Inc. and Equifax Canada, which plainly demonstrated the existence of practices which were not ISO 27001 compliant. These multiple security deficiencies were significant, and had clearly been present for an extended period of time. See Section 5 of this report for further details.
- In the context of this additional knowledge by Equifax Canada, it was therefore not reasonable for it to rely on the ISO 27001 certification as assurance of adequate security by Equifax Inc. Cognizant of such poor practices, Equifax Canada should have taken further measures to assess the security of Canadian personal information held by Equifax Inc. and ensure that any necessary corrective measures were taken in a timely way.
- Consequently, with respect to Equifax Canada’s accountability for personal information under its control handled by Equifax Inc., the matter is well-founded.
- Since the breach, in response to our preliminary recommendations, Equifax Canada and Equifax Inc. have taken steps to develop a written arrangement covering the elements described in para. 74 above. They have also taken steps to improve general oversight and accountability for privacy practices, including appointing an Equifax Inc. Chief Privacy Officer and supporting team. In relation to personal information collected by Equifax Inc. in the course of processing payments for Equifax Canada fraud alerts, Equifax Canada has subsequently changed its payment processing arrangements such that Equifax Inc. does not process such payments for Equifax Canada. In addition, it is no longer charging individuals a fee to place fraud alerts on their credit file.
Recommendations
- The following recommendations relate to contraventions found in Sections 1, 2, and 3 of this report. In considering our recommendations, we took into account the limited choices for Canadians with respect to credit reporting products in Canada and the risk to Canadians, given the sensitive, high value information held by Equifax Inc. We also considered the systemic and long-term nature of the issues identified, many of which Equifax Canada and Equifax Inc. had been aware of, but failed to correct in a timely way. Given the risks to Canadians, long-term monitoring will be critical towards rebuilding trust in Equifax Canada and Equifax Inc.’s internal oversight capacity and establishing a “security culture” that endures. We therefore recommend that Equifax Canada:
- Implement a procedure to keep the written arrangement with Equifax Inc., covering all Canadian personal information under Equifax Canada’s control collected by Equifax Inc. and disclosed to Equifax Inc., up-to-date.
- Institute a robust monitoring program by Equifax Canada against the requirements in the arrangement, and a structured framework for addressing any issues arising under it.
- Identify Canadians’ personal information that should no longer be retained by Equifax Inc. according to its retention schedule and delete it.
- Every two years, for a six-year term, provide to our Office:
- a report from Equifax Canada detailing its monitoring for compliance with the arrangement described in b. above;
- an audit report and certification, covering all Canadians’ personal information processed by Equifax Inc., against an acceptable security standard, conducted by an appropriate external auditor; and
- a third party assessment, covering all Canadians’ personal information processed by Equifax Inc., of Equifax Inc.’s retention practices.
Section 4. Consent Obtained from Canadians for Disclosure of Information to Equifax Inc.
- PIPEDA Principle 3 – Consent, requires the knowledge and consent of the individual for the collection, use, or disclosure of personal information, except where inappropriate. Section 6.1 of PIPEDA further specifies that the consent of an individual is only valid if it is reasonable to expect that an individual to whom the organization’s activities are directed would understand the nature, purpose and consequences of the collection, use or disclosure of personal information to which they are consenting.
- One complainant in this matter noted with concern that when she asked how her information came to be in the US after signing-up for Equifax Canada products on an Equifax.ca website, neither the agent she spoke to, nor their supervisor, could explain. The sharing of personal information with multiple parties carries inherent risks (such as increased exposure to cyber-attacks), and a key goal of the consent provision in PIPEDA is to empower Canadians to make choices concerning who has their personal information and why. In this context we examined the disclosures of Canadian information to Equifax Inc., and the consent obtained for these disclosures.
- As discussed in Section 3 of this report (para. 58), we are of the view that for the purposes of personal information handling under PIPEDA, Equifax Canada and Equifax Inc. are third parties to each other.
- As described in Section 3 of this report, Equifax Inc. received the personal information of Canadian consumers in two ways. First, it received information directly from Canadian consumers when they applied for products through the Global Consumer Solutions (“GCS”) system, and second, it received credit reporting information transferred to it by Equifax Canada about those consumers to fulfil those products. Also as described in Section 3 of this report, Equifax Canada remained accountable for this information transferred to Equifax Inc. for processing, and responsible for the related obligations under PIPEDA 4.1.3.
- At the same time, these transfers for processing from Equifax Canada to Equifax Inc. constitute disclosures of personal information under the meaning of PIPEDA Sections 7(3), and 4.3.Footnote 13
- Notwithstanding the significant disclosure of information to Equifax Inc. during this process, the GCS portal is displayed to consumers on “Equifax.ca” domain pages, with an Equifax Canada Privacy Policy and Terms of Use (see Figure 2). Other than in the Privacy Policy and Site Terms of Use, at the time of the breach, there was no indication to consumers at any time in the process that their information was being collected by or disclosed to Equifax Inc. in the US.
- Equifax Canada notes that its affiliation with Equifax Inc. is also signaled to consumers by a copyright note in the footer of all Equifax.ca websites, including pages describing both products delivered directly by Equifax Canada, and those delivered through Equifax Inc, that says: “Copyright [date] Equifax Inc. All rights reserved. Equifax and the Equifax marks used herein are trademarks of Equifax Inc.” However, consumers would not reasonably expect or look to a copyright notice in a footer for notice of a transfer of information to a third party.

- As described in para. 65 above, the Terms of Use available to Canadian consumers at the time of the breach specified that “…the products and product features (“Product” or “Products”) available via this Site are provided by Equifax Canada Co. (“Equifax”). We may also partner with other companies (“Suppliers”) or affiliates (“Equifax Affiliates”) to provide Products to you or sell you a Product provided by a Supplier or an Equifax Affiliate.” The Equifax Canada Privacy Policy, which identified the Equifax Canada Chief Privacy Officer as the contact point for privacy matters indicated that: “This privacy policy is published to inform you of the practices and procedures we, Equifax Canada, its parent company and affiliates (“Equifax”, “we”, “us”, “our”) maintain in respect of the collection, use and disclosure of personal information.”
- Also as noted above, Equifax Inc. and Equifax Canada indicated to us that they informed individuals about the transfer of their personal information outside of Canada through the following statement in the Equifax Canada Privacy Policy: “In the event that we transfer your personal information to a third party in Canada or across borders for processing, we contractually require such third party to protect your personal information in a manner consistent with our privacy safeguarding measures, subject to the law of the third party jurisdiction.”
- At issue, with respect to consent, is whether the explanations provided to individuals about the collection by, and transfer to, Equifax Inc. of their personal information was adequate for their consent to be valid under Principle 3 and Section 6.1 of PIPEDA. We are of the view that it is not valid, for the following reasons.
- Under the Consent Principle, Sections 4.3.4 and 4.3.5, the form of consent sought must take into account the sensitivity of the information, and the reasonable expectations of the individual are also relevant. More robust, express, consent is required for the collection and disclosure of more sensitive information and for information that an individual would not reasonably expect to be collected by, or disclosed to, a particular organization in the context of the product or service sought. As noted in Section 1 of this report, the information collected by, and disclosed to, Equifax Inc. is sensitive. We are of the view that given the extent to which the GCS portal was presented to Canadians as being operated by Equifax Canada directly (see paras. 102-105), individuals may have been surprised to learn about the disclosures made. Individuals obtaining these products would not reasonably expect, given the indications to the contrary, that sensitive information was being collected by, and disclosed to, a third party outside of Canada (even in the context of the parent-subsidiary relationship). Therefore, in our view, express consent is required.
- Under Section 6.1., for consent to a collection or disclosure to be valid, individuals must be provided with enough information to understand the nature, purpose and consequences of the collection or disclosure. In our view, even an individual who carefully reviewed both the Privacy Policy and Terms of Use available to individuals at the time of the breach would not be able to understand that, without exception, their information was being collected by Equifax Inc., in the US, with immediate effect. Nor would they understand that substantial further information would subsequently be disclosed by Equifax Canada to Equifax Inc., or that there would be no further details provided or consent sought before such disclosures occurred. Given the extent of the collection and disclosure of sensitive personal information, such clarity is, in our view, clearly warranted in this case.
- Providing adequate information about available choices when an individual is consenting to the collection, use or disclosure of their information is a key component of valid consent. In this case, it appears reasonable to require consent to the collection of information by, and disclosure of information to, Equifax Inc. as a condition of the online Canadian direct-to-consumer products, as Equifax Canada does not offer these products in-house. However, an individual would still have choices. In addition to the simple option of “not signing-up” for Equifax Canada credit file monitoring or other products, individuals interested in obtaining access to their Equifax Canada credit report could choose to use Equifax Canada’s free credit report service, provided by postal mail and avoiding any information disclosure to Equifax Inc. Equifax Canada does not currently communicate the difference in disclosures to consumers in the course of delivering online or postal access, i.e., that the former involves collection of information by Equifax Inc. and transfers of information to Equifax Inc. in the US, whereas the latter does not.
- In summary, Equifax Canada was not adequately clear about: (i) the collection of sensitive personal information by Equifax Inc., in the US, (ii) its subsequent disclosures of sensitive personal information to Equifax Inc., and (iii) the options available to individuals who do not wish to have their information disclosed in this way. Consequently, with respect to Equifax Canada’s practices to obtain consent for collection of personal information by Equifax Inc., and disclosure of personal information to Equifax Inc., the matter is well-founded.
- However, as noted in para. 101 above, we acknowledge that in previous guidance our Office has characterized transfers for processing as a ‘use’ of personal information rather than a disclosure of personal information. Our guidance has also previously indicated that such transfers did not, in and of themselves, require consent. In this context, we determined that Equifax Canada was acting in good faith in not seeking express consent for these disclosures.
Recommendations
- We recommend that Equifax Canada and Equifax Inc.:
- Revise their communications to individuals purchasing or accessing direct-to-consumer products to seek valid express consent for any collection by, or disclosures to, Equifax Inc. of personal information, including clearly explaining the nature and purpose of the collection by, and disclosure to, Equifax Inc. in the US of Canadian personal information. To the extent that individuals can obtain similar services from Equifax Canada without the need for such transfers, individuals should be informed of these options at the time consent is sought.
- Seek valid, express consent from any current customers for future disclosures of their information to Equifax Inc.
Section 5. Safeguards of Personal Information by Equifax Canada
- Under the PIPEDA Safeguards Principle (4.7), as described in Section 1 of this report, personal information must be protected by security safeguards appropriate to the sensitivity of the information. As described in Section 1, the information held by Equifax Canada as a credit reporting agency (“CRA”) is sensitive.
- Given the high level of integration of safeguards between Equifax Canada and Equifax Inc., we examined Equifax Canada’s safeguards for data it holds directly in order to assess whether similar security deficiencies were found with the subsidiary.
Oversight
- As highlighted in Section 1 of this report, an effective security program must include adequate oversight mechanisms to ensure that the program is, and remains, appropriate to the sensitivity of the information held and the security threats faced. For an organization protecting significant volumes of sensitive personal information, as is the case for Equifax Canada, in our view the following high level oversight mechanisms, or alternative equivalent measures, would be required under PIPEDA’s safeguards principle:
- at least annually, a comprehensive internal assessment of the full security program, and at least every two years, a comprehensive external security audit;
- regular internal and external penetration testing (frequency based on context, including risk assessment and complexity), including comprehensive external penetration testing at least annually.
- In order to assess Equifax Canada’s oversight mechanisms, we therefore asked Equifax Canada to provide us with copies of any internal or external testing/assessments/audits/certifications of their safeguards, threats, and/or risks conducted in the past five years. In response, Equifax Canada provided:
- Equifax Inc.’s global ISO 27001 compliance certificates and related documents before and after the breach, which covered Equifax Canada;
- Annual Equifax Canada PCI-DSS compliance certificates and related audit reports;
- Annual Equifax Inc. global external penetration test reports and related remediation reports, which covered Equifax Canada;
- Annual Equifax Canada specific internal penetration test reports;
- Two targeted security risk assessments, commissioned by Equifax Inc. Internal Audit, which specifically examined Equifax Canada systems, among other sites.
- In our view, for the reasons described below, the combination of the above measures (para. 116) was insufficient for an organization safeguarding the volume and sensitivity of personal information that Equifax Canada holds.
Oversight - Internal and External Security Assessments
- First, the ISO 27001 certification process in place at the time of the breach was a global certification, carried out for Equifax Inc. for all of its sites (across more than 13 countries, including Equifax Canada sites). The process was conducted on a sampling basis. Because of this methodology, Equifax Canada’s Toronto headquarters operations, where the majority of its IT security staff are located, had not been sampled since at least 2014. The process would therefore not have been able to provide adequate site-specific feedback to assess and inform Equifax Canada’s specific security program.
- Second, as described in Section 3 of this report, the certification in place at the time of the breach indicated that Equifax’s global operations, including Equifax Canada, had been ISO 27001 compliant since at least 2011. However, Equifax Canada was also privy to contradictory information resulting from: (i) external penetration testing, and (ii) the two external assessments. These described practices, including ones at Equifax Canada specifically, which were not ISO 27001 compliant. Further detail is provided below (in para. 122 - 141).
- Third, with respect to Equifax Canada’s PCI-DSS certification, this certification is limited to assessing the adequate protection of payment card information, and is therefore not comprehensive enough by itself to ensure the effectiveness of an overall security program which must also protect non-payment card information. We further note with concern that this certification process, which is normally carried out on an annual basis in accordance with industry standards, has not been conducted for Equifax Canada’s systems since September 2016. Equifax Canada cited the need to focus on improving its overall security as the reason for deferring this certification process.
- Equifax Canada represented that in the last five years, its security oversight was also supported by two assessments commissioned by Equifax Inc. and conducted by leading audit firms. These assessed specific security measures and geographic sites identified by Equifax Inc. based on risk profile. The two assessments were both conducted in 2015-2016. While neither provides the kind of comprehensive scope necessary for a fulsome evaluation of a security program, such targeted audits are important tools for addressing risks identified. In our view it is a positive step that Equifax Inc. commissioned these targeted reviews in order to better understand key risk areas. We note with concern that prior to these two assessments, no other such assessments covering Equifax Canada’s operations appear to have been performed within the last five years.
Oversight - Internal and External Penetration Testing
- Fundamentally, penetration testing is an authorized simulated attack on an organization’s systems and is used to evaluate the security of the system. To be useful, penetration testing needs to be informed by tools and techniques known to be used by attackers. The external penetration testing covering Equifax Canada appears, in our view, to be both comprehensive and of an appropriate frequency (annual). The internal penetration testing specific to Equifax Canada at the time of the breach had two major deficiencies:
- It should have been conducted more often than once a year considering the context, which included a high volume of sensitive information and risks identified; and
- It did not include basic, necessary components of penetration testing. The testing conducted did not include the use of any exploitation tools used by attackers, and overall, employed a very limited menu of tools and techniques.
- In our view, for the reasons set out above (para. 118 - 122), the oversight mechanisms in place for Equifax Canada’s security program were inadequate.
Vulnerability Management
- Our investigation also assessed Equifax Canada’s vulnerability management, in light of the failure of Equifax Inc. to patch a known vulnerability.
- First, we examined whether the specific patch missed in the Equifax Inc. incident was missed by Equifax Canada. Equifax Canada confirmed that it had no infrastructure using the Apache Strut software, and therefore had not needed to apply that patch.
- Second, we examined copies of the previous two years of external and internal penetration testing covering the Equifax Canada systems, in part to assess whether other unaddressed external vulnerabilities existed, which would be indicative of a systemic problem in vulnerability management at Equifax Canada.
- Equifax Canada’s vulnerability management program was highly integrated with that of Equifax Inc. Equifax Canada conducted vulnerability scanning and patching using the tools and procedures provided by Equifax Inc., and the final step of checking to confirm that vulnerabilities had been addressed was conducted by Equifax Inc. staff in the US.
- Equifax’s global external penetration tests (December 2015 and December 2016), which covered Equifax Canada, both highlighted serious systemic concerns. The 2015 report found that the Equifax external network did not meet its security objectives, and the 2016 report made it clear that the situation remained inadequate one year later, noting certain findings that were previously identified to Equifax Inc. As late as July 2017, after the breach was underway but not yet detected, a follow-up remediation report on the identified vulnerabilities indicated that certain high risk vulnerabilities had still been only partially remediated.
- Given the high level of integration of Equifax Canada and Equifax Inc. vulnerability management, the overarching inadequacies identified in the above penetration testing reports are clear indicators that Equifax Canada’s vulnerability management program was inadequate at the time of the breach.
- Equifax Inc. also commissioned an external perimeter Assessment, completed in January 2016, by a third party audit firm, which focused on Equifax Canada’s operations, among other locations. Consistent with the broad penetration testing results above, this assessment identified multiple high and medium vulnerability management program security risks specific to Equifax Canada.Footnote 14
- It found multiple inadequate practices, including in some internet facing devices, and concluded that based on the observations made, the overall Equifax perimeter cyber security posture observed at locations including Equifax Canada appeared to be below average for the financial technology industry. Ensuring that internet-facing devices do not have exploitable vulnerabilities is important in preventing successful cyber-attacks.
- In light of the above (para. 127 - 131), it is our view that the vulnerability management system in place to protect Canadian personal information held directly by Equifax Canada was inadequate considering the volume and sensitivity of the personal information held.
Network Segregation
- First, our investigation assessed whether a similar network segregation issue existed at Equifax Canada as was identified at Equifax Inc. Due to the more limited range of products and services offered directly by Equifax Canada, including the lack of a direct-to-consumer internet portal, we did not identify the specific network segregation issue found at Equifax Inc. at Equifax Canada.
- Second, we examined Equifax Canada’s network segregation more generally. We found no indications of failings with respect to network segregation during our investigation.
Implementation of Basic Information Security Practices
- First, our investigation examined Equifax Canada’s use of any ‘file shares’ for indicators of similar basic deficiencies identified with respect to Equifax Inc.’s use of its ‘file share’. This examination did not find any indicators that Equifax Canada’s use of a ‘file share’ was subject to the types of deficiencies identified at Equifax Inc.
- Equifax Canada indicated it provided its employees with training on appropriate handling of data, but confirmed that, as with Equifax Inc., it did not have specific training material covering the topic of appropriate use of the ‘file share’. Equifax Canada volunteered a sample of its security training for staff, on the topic of payment card security. We were surprised to see that the training was an off-the-shelf product designed for front line retail staff and supervisors which had not been tailored to Equifax Canada’s substantially different role vis à vis the handling of payment card information. Specifically, Equifax Canada handles credit card account numbers as part of the information held in a consumer’s credit file, not in the context of accepting payment for products or services by credit card.
- Second, we examined the two assessment reports provided by Equifax Canada (listed above in para. 116). Both of these assessments, conducted by third party audit firms, reported multiple high security risks and a range of medium security risks across a broad range of practices at Equifax Canada.
- One of these, an external Perimeter Security Assessment, found multiple instances of inadequate security practices (described above in para. 130 - 131).
- The other reviewed whether practices in certain Equifax sites were secure and compliant with Equifax Inc.’s global security policies and standards across certain business/IT processes material to the protection of personal information for a diverse range of activities.
- This Assessment, which examined practices using a range of risk criteria, found high overall risk at Equifax Canada in more than a third of the processes, and medium overall risk in another third. The report highlighted that Equifax Canada’s information security team had limited resources and that business and IT staff were in need of ongoing training and awareness.
- As noted earlier, it is a positive step that Equifax Inc., which commissioned both of these assessments, was assessing risk areas identified in more detail. However, the extent of the deficiencies identified in both reports, across a range of different processes, is unacceptably high for an organization holding personal information of the scope and sensitivity held by Equifax Canada.
Conclusion
- For the reasons described above, we are of the view that Equifax Canada was lacking adequate safeguards for the protection of personal information it holds in three of the areas described above:
- oversight;
- vulnerability management; and
- implementation of basic information security practices.
- In our view, the specific weaknesses described above individually and collectively constitute failures to implement appropriate security safeguards given the volume and sensitivity of the personal information held by Equifax Canada. Consequently, in relation to the safeguards of personal information by Equifax Canada, the matter is well-founded.
- Since the breach, Equifax Canada had initiated a range of steps to improve its security program, including:
- significantly increasing its IT security staff;
- participating in Equifax Inc. led efforts to improve security practices (as described in Section 1 of this report); and
- initiating an Equifax Canada specific ISO 27001 certification process.
- While the above are positive steps, in light of the serious deficiencies found, which are indicative of long-term, systemic issues, we are of the view that additional assurances are required to ensure Equifax Canada’s safeguards are brought up to an adequate level.
Recommendations:
- Similar to our analysis in Section 3 of this report, in considering our recommendations, we took into account the limited choice Canadians have regarding their information being collected by credit monitoring agencies in general. That is, if they choose to participate in the lending economy, credit agencies will generally collect their sensitive information.
- We also considered the serious and systemic nature of the issues identified, many of which Equifax Canada had been aware of, but failed to correct in a timely way. Given the risks to Canadians, long-term monitoring will be critical towards rebuilding trust in Equifax Canada’s internal oversight capacity and establishing a “security culture” that endures. We therefore recommend that Equifax Canada:
Provide our office with a detailed security audit report and certification, covering all Canadian personal information it is responsible for, against an acceptable security standard, conducted by an appropriate external auditor every two years for a six-year term.
Section 6. Adequacy of Post-Breach Safeguards to Protect Against Unauthorized Use
- Under the PIPEDA Safeguards Principle 4.7.1, an organization must implement security safeguards to protect personal information against loss or theft, as well as unauthorized access, disclosure, copying, use, or modification. [emphasis added]. In our view, this provision therefore requires organizations to undertake appropriate mitigation measures after a breach to protect against future unauthorized use of the compromised personal information by malicious actors.
- Although there were variations in what personal information was compromised for affected Canadians, most had at least their names, addresses, dates of birth and social insurance numbers compromised. As discussed in Section 1 of this report, these identifiers, combined, present a real risk of unauthorized use by malicious actors for identity theft.Footnote 15 This risk is enduring because these identifiers are often used for the purpose of identity validation, and are relatively permanent.
- In this context, we examined whether the protections offered to affected Canadians by Equifax Canada were adequate to protect the compromised personal information against such potential unauthorized use over the long-term.
- Equifax Canada directly notified all Canadians who had been identified as being affected by the breach, providing them with a detailed description of what personal information was breached in their specific case. It also offered all affected Canadians free credit monitoring with Equifax Canada for one year. It subsequently extended the credit monitoring for individuals who had signed up for it to two years.
- For American consumers, in addition to an initial one year of credit monitoring, Equifax Inc. subsequently extended free credit monitoring for individuals who signed up for it to two years. It has also offered consumers a new, free “Lock & Alert” service. Equifax Inc.’s website says: “Lock & Alert was created with a simple premise: that you should be able to conveniently control access to your Equifax credit report, for life, and for free.” Online or through an app, an individual can lock and unlock their credit file on demand. Locking their file prevents most organizations from accessing their information (such as for a credit check). This provides enduring protection against identity theft by limiting the ability of identity thieves to obtain the credit check normally required to get a loan in someone’s name.
- Several complainants raised concerns about the post-breach remediation measures offered by Equifax Canada to Canadians. Concerns included the unavailability of a credit freeze option (like the Lock & Alert above), and the length of credit monitoring - as thieves might simply wait until after the one year of credit monitoring had elapsed to make use of the information. In our view, this is a valid concern.
- Equifax Canada argued that one year of credit monitoring alone is reasonable, as it the usual period offered by organizations, including federal government institutions, after a breachFootnote 16. However, given the pivotal industry role of Equifax Canada that centers on the amassing, use and disclosure of sensitive credit and credit-related personal information, such comparisons are of limited relevance. Further, Equifax Canada provided no information as to the efficacy of the one-year period in preventing identity theft.
- With respect to the Lock & Alert product, Equifax Canada indicated that while a law has been passed to require CRAs to offer credit freezes in Ontario, that law is not yet in force, pending the development of regulations. It argued that if only Equifax Canada were to offer a Lock & Alert type product, prior to credit freezes being required by law, that lenders could simply check an individual’s credit through a different Canadian CRA if it found access to Equifax Canada’s credit file had been locked by an individual. It indicated it would therefore explore creating something similar “as Canadian law develops.”
- Equifax Canada also noted that Canadian consumers can already put a six-year fraud alert on their Equifax Canada credit file (currently offered for free). A fraud alert obliges organizations conducting a credit check to take specified measures to contact the individual for identity verification before extending credit. A failure to follow the fraud alert instructions would be a violation of Equifax Canada’s terms of service with its members (organizations) and could result in punitive action by Equifax Canada, if reported. However, unlike a credit freeze, a fraud alert does not enable consumers to prevent access to their credit file for an unauthorized credit check, and a consumer can only put a fraud alert on their file if they believe they have already been a victim of fraud or identity theft.
- In light of the above context, for the reasons set out below, we are of the view that Equifax Canada is obliged to do more to provide lasting protection to affected Canadians than offering a brief period of credit monitoring.
- First, as described above, as a CRA, Equifax Canada has a wider array of tools at its disposal to safeguard against the unauthorized use of compromised personal identifiers for the purpose of credit identity theft. This is largely due to its ability, as the largest CRA in Canada, to help prevent fraudulent credit checks.
- Second, for consumers in the United States, Equifax Inc. itself, in recognition of the enduring risk to consumers from the breach, and in recognition of its wider array of tools as a CRA, proactively offered American consumers a free and accessible credit freeze product ‘for life’. Affected Canadians face materially the same risks as affected Americans.
- Third, while CRA’s are not yet obliged to offer credit freezes in Canada, it clearly represents a protective measure against the enduring risk to affected individuals that resulted from the safeguards failures by Equifax Canada and Equifax Inc., and appropriate to Equifax Canada’s pivotal role as a CRA.
- Therefore, with respect to safeguards against unauthorized use of the compromised Canadian information, the matter is well-founded.
Recommendation
- In considering our recommendation with respect to this matter, we took into account two factors. First, as described in para. 148, in our view, provision 4.7.1 of PIPEDA requires organizations to undertake appropriate mitigation measures after a breach to protect against future unauthorized use of the compromised personal information by malicious actors. Second, we considered the need for appropriate remedial measures by Equifax Canada to reduce the risk of harm to individuals stemming from the contraventions with respect to safeguards, retention, accountability and consent found in Sections 1 through 5 of this report. We therefore recommended that Equifax Canada offer all affected individuals a form of lasting protection against identity theft, which in our view, would be accomplished via a free- or low-cost credit freeze product in addition to extended credit monitoring.
Conclusion
- Equifax Canada has signed a compliance agreement committing to undertake a range of corrective measures with respect to the contraventions described in this report. On the basis of these commitments, with respect to the findings in Sections 1 through 5 of this report, we find the matters well-founded and conditionally resolved. With respect to the finding in Section 6, we find the matter well-founded and partially resolved as Equifax Canada has committed to provide extended credit monitoring of at least 4 years, but has not agreed to provide a free- or low-cost credit freeze product.
Summary of Recommendations
- The following recommendations relate to contraventions found in Sections 1, 2, and 3 of this report, i.e. Safeguards and Retention by Equifax Inc. and Accountability of Equifax Canada. We recommended that Equifax Canada:
- Implement a procedure to keep the written arrangement with Equifax Inc., covering all Canadian personal information under Equifax Canada’s control collected by Equifax Inc. and disclosed to Equifax Inc., up-to-date.
- Institute a robust monitoring program by Equifax Canada against the requirements in the arrangement, and a structured framework for addressing any issues arising under it.
- Identify Canadians’ personal information that should no longer be retained by Equifax Inc. according to its retention schedule and delete it.
- Every two years, for a six-year term, provide to our Office:
- a report from Equifax Canada detailing its monitoring for compliance with the arrangement described in b. above;
- an audit report and certification, covering all Canadians’ personal information processed by Equifax Inc., against an acceptable security standard, conducted by an appropriate external auditor; and
- a third party assessment, covering all Canadians’ personal information processed by Equifax Inc., of Equifax Inc.’s retention practices.
- The following recommendations relate to contraventions found in Section 5 of this report, ie. Safeguards of Equifax Canada. We recommended that Equifax Canada:
- Provide our office with a detailed security audit report and certification, covering all Canadian personal information it is responsible for, against an acceptable security standard, conducted by an appropriate external auditor every two years for a six-year term.
- Date modified:

